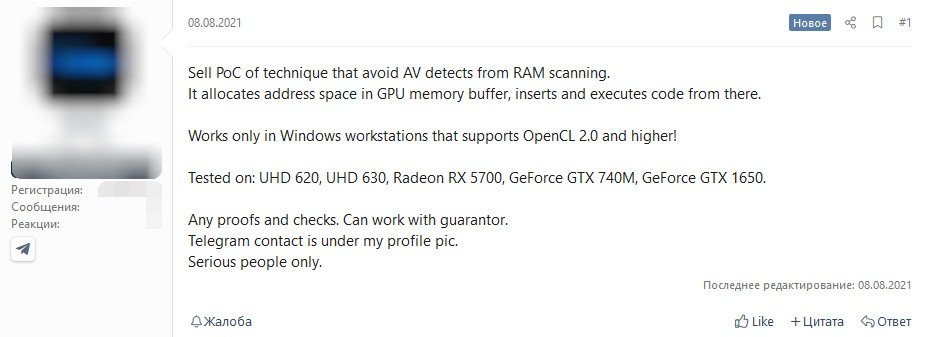
According to Bleeping Computer, cybercriminals have found a new way to hide malware in graphics cards memory. This method of utilizing graphics card memory instead of system memory is undetectable by the antivirus software, the original advertisement on hacking forums claims.
The malware uses graphics memory allocation space, from where the code is executed. The technology uses OpenCL 2.0 API on Windows operating system, no other systems are affected by the malicious code.
The hacker confirmed that the code has been tested on Intel UHD 620/630 graphics as well as Radeon RX 5700 GPU and GeForce GTX 740M and GTX 1650 discrete cards. It is unclear if other graphics cards are affected, but assuming that this method uses OpenCL 2.0, it is very likely to be compatible with other modern GPUs.
Read more…